
How to Integrate Red Teaming in Your Security Program
Table of contents
Introduction – What Red Teaming Is and Why You Should Care
As a CISO, you have to ensure your organization’s data and infrastructure are as secure as possible against cyber threats and that you are as prepared as possible to respond to the inevitable attack.
A robust security program is key to achieving this goal. It should include a wide range of technical and procedural controls designed to detect, prevent, but also to respond to and to mitigate the impact of cyber-attacks.
Building and maintaining an effective security program requires experience; it is not a one-off task. It requires ongoing assessments and adaptation to respond to evolving threats and changing business needs.
A red teaming exercise is an objective-driven realistic engagement that combines offensive tactics and techniques to perform a vertical assessment of a company’s security posture. While penetration testing focuses on the technology layer, red teaming exercises aim to test all layers that comprise an organization’s security posture (figure 1).
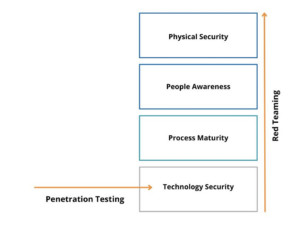
Figure 1. Red teaming exercises test all layers of the organization’s security posture
Red teaming exercises should be part of your assessment toolkit, a regular feature on your planning calendar that will help ensure you are as prepared as possible. Red teaming exercises are simulated attacks designed to identify vulnerabilities and test an organization’s security against real-world threats. By simulating attacks in a controlled environment, red teaming exercises can help you better understand the organization’s security posture, identify gaps in protecting valuable assets as well as in already established and operating procedures. Red teaming exercises can help address challenges of both organizations with mature security programs but also less experienced companies just starting their security journey.
In this article, we’ll provide a comprehensive guide to how you can incorporate red teaming exercises into your security program, from planning and preparation to execution and analyze. By following these guidelines, you can ensure that your organization is better prepared to defend against cyber threats.
Red Team Planning and Preparation
Define Your Goals
To ensure the success of a red team exercise, it is essential to define objectives, and the approaches which should be followed. This will ensure the exercise is focused and produces actionable results, which fit your current cybersecurity challenges.
Some key questions to consider when defining objectives, could be:
- From what perspective do you want to test your organization? For example, do you want to understand how an external attacker could breach your external perimeter? Or maybe you are more interested to test it in an Assumed Breach mode with the goal of highlighting weaknesses, from a malicious insider perspective? What about your physical perimeter? Could a malicious outsider gain physical access to your sensitive production sites?
- What specific goals do you want to achieve? Gaining visibility on your organization’s internet-facing attack surface? Testing the effectiveness of your incident response plan? Testing awareness and reaction of employees during a social engineering campaign? Or simply wondering how your company can get hacked in a real-world targeted attack context?
- What is your schedule? Are you looking for a single snapshot of the security with a fairly short time boxed mission? Or you are more concerned about what a real attacker could do in a continuous red teaming scenario?
By answering these questions, you will be able to design a tailored red team engagement for your organization needs.
Identify Participants
It’s important to carefully select participants who will take part to the exercise to make it as realistic as possible.
When defining such actors, the following element should be considered.
- Red Team: The team in charge to simulate aggressors and perform necessary attacks to achieve defined goals. This team should have solid experience in offensive security as well as enough inventiveness to provide attacks path a real attacker could use to compromise the company.
- Blue Team: The team who will defend and monitor the organization to detect and react to attacks. They should have a strong understanding of your organization’s security controls and be able to respond to different types of attacks to prevent or contain an eventual incident.
Please note that a blue team is not mandatory for a red team engagement, however, if the objective is to test detection and processes during a potential breach, then the involvement of your blue team will increase the value of such exercise.
Establish Rules of Engagement
Even if by nature, a red team mission is designed to give attackers freedom on techniques and targets, a Rules of Engagement document should be defined so that the exercise is conducted safely.
Such a document is particularly important if you need to exclude some assets or attacking techniques from the scope of the mission. As an example, you could exclude physical intrusions or social engineering campaigns. Rules of Engagement could also specify if specific parts of the company should not be tested. You might wish to exclude sensitive production sites, for example. However, keep in mind that restraining the scope of the mission too much could falsify results and restrict the ability of the teams to detect blind spots.
Finally, the document should define a plan in case the red team exercises take an unexpected turn. It could be possible that the red team operators get caught during exploitation attempts, for example. What should they do then? Continue with a white box approach or shutdown operations?
By establishing clear rules of engagement, you can ensure that the red teaming exercise is conducted in a controlled manner.
Communicate the Purpose and Scope
It’s important to communicate the purpose and scope of the red teaming exercise to key stakeholders. However, to keep the red team exercise as realistic as possible, only generic information about the mission should be communicated internally. On real world scenarios, normally, attackers do not advertise dates and objectives before starting an attack.
Execution – How to Run a Red Team Engagement
The red team should simulate the attacks as realistically as possible, using a variety of techniques, tactics, and procedures. Common phases of a red team mission can vary depending on the specific objectives. However, they typically include:
- Planning and Reconnaissance
- Initial Access
- Escalation and Lateral Movement
- Persistence and Evasion
- Data Exfiltration
- Reporting
If a blue team takes part in the mission, they should monitor, document, and detect malicious activities, just as they would during standard day-to-day business operations. They should follow procedures and reporting processes in place.
Debriefing
As the CISO, the debriefing stage is where you can gain the most value from the red teaming exercise. The purpose of the debriefing is to analyze the results of the exercise, identify any weaknesses or vulnerabilities in your organization’s infrastructure or process, and develop recommendations for improvement.
You should focus on identifying any weaknesses or vulnerabilities in your organization’s security program that were exposed during the exercise. This could include gaps in policies and procedures, weaknesses in security controls, or human error.
The debriefing should evaluate the effectiveness of your organization’s security controls in detecting and responding to the red team’s attacks. This could include analyzing the response time of your Incident Response team, the effectiveness of your monitoring and detection tools, or the response of your Physical Security teams.
Finally, you should focus on developing recommendations for improvement to your organization’s security program. This could include updating policies and procedures, implementing new security controls, or providing training and awareness programs for employees.
By conducting a thorough debriefing, you can gain valuable insights into the effectiveness of your organization’s security program and develop a roadmap for improving your overall security posture.
Conclusion
Integrating red teaming into your security program can provide valuable insights into the effectiveness of your organization’s security controls and help identify weaknesses and vulnerabilities that could be exploited by real-world attackers. By following the key steps outlined in this article, you can prepare for and execute a successful red teaming exercise to obtain valuable results to improve the overall security of your company.
Remember to engage with your red and blue teams throughout the exercise. By taking a proactive approach to security testing and continuously improving your security program, you can stay one step ahead of potential threats and protect your organization’s critical assets.







